
Game theoretic solution for an Unmanned Aerial Vehicle network host under DDoS attack - ScienceDirect

Run time variation with increasing number of UAVs for DDoS attack (same... | Download Scientific Diagram
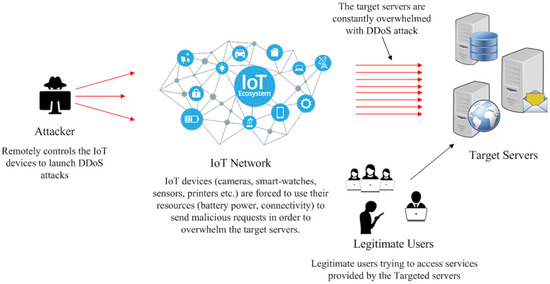
Sensors | Free Full-Text | Blockchain Based Solutions to Mitigate Distributed Denial of Service (DDoS) Attacks in the Internet of Things (IoT): A Survey
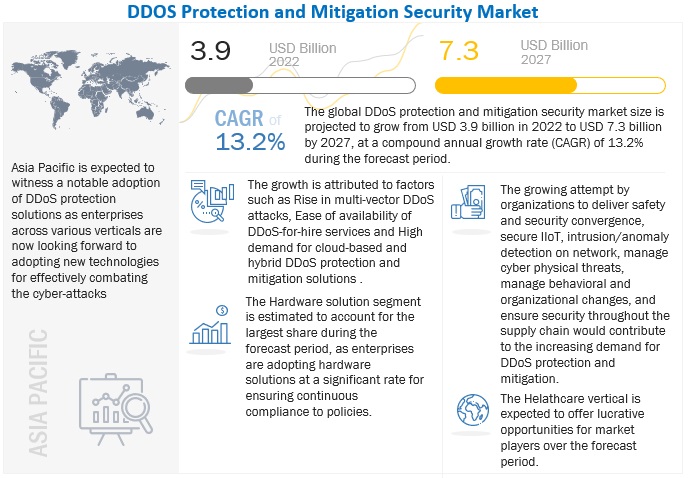
DDoS Protection and Mitigation Market Size, Share and Global Market Forecast to 2026 | MarketsandMarkets

Drone demo shows it's possible to protect 5G-managed devices from DDoS, exfiltration attacks | Network World

GitHub suffers from a DDoS attack, Amazon moves drones to Canada, IBM Watson acquires Blekko—SD Times news digest: March 30, 2015 - SD Times
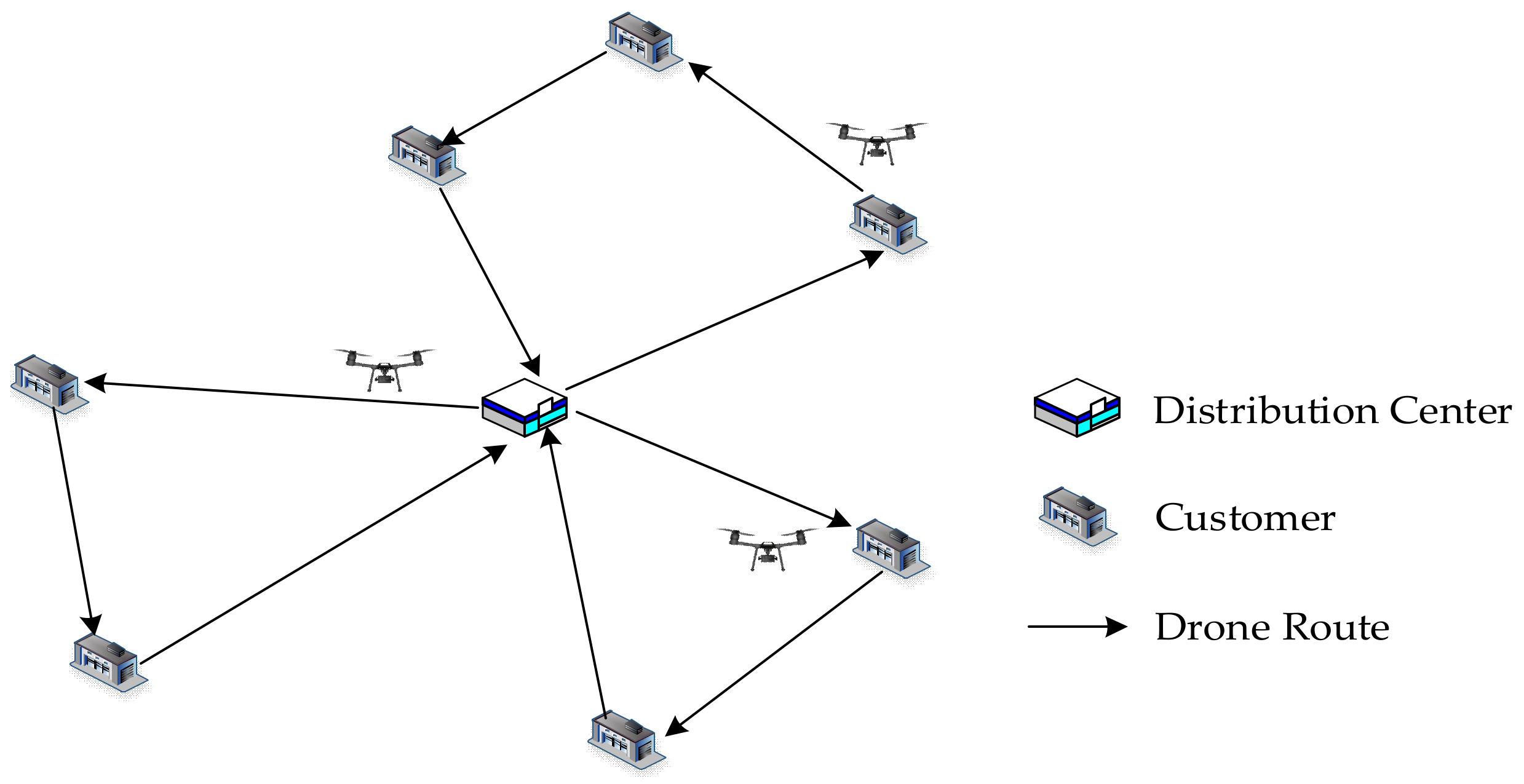
Sustainability | Free Full-Text | Optimal Model and Algorithm of Medical Materials Delivery Drone Routing Problem under Major Public Health Emergencies | HTML

Sensors | Free Full-Text | D-CEWS: DEVS-Based Cyber-Electronic Warfare M&S Framework for Enhanced Communication Effectiveness Analysis in Battlefield | HTML
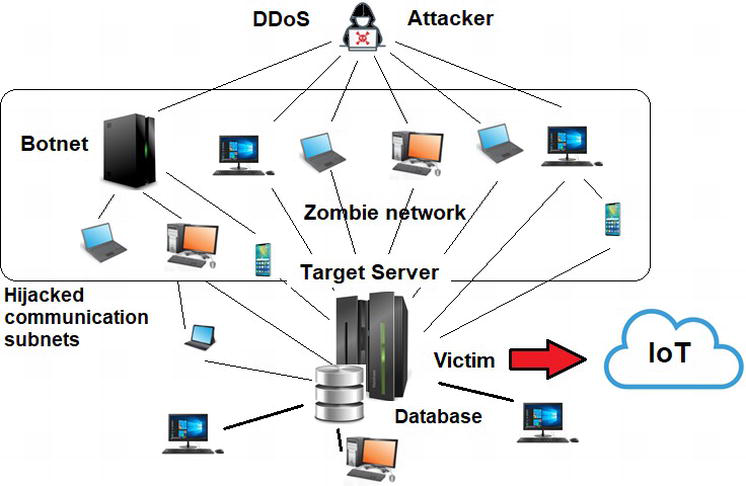




![Denial of service (DoS) attack [78] | Download Scientific Diagram Denial of service (DoS) attack [78] | Download Scientific Diagram](https://www.researchgate.net/profile/Phuoc-Dai-Nguyen/publication/349419829/figure/fig2/AS:1001946601238529@1615894093911/Denial-of-service-DoS-attack-78.png)




